They’re finally here! Gmail was one of the last services to add blue checkmarks. But that was the thing a lot of people needed even more than checkmarks on social media. As we’re using our emails primarily to get information from a bunch of services, government offices, and other routine but mandatory stuff, our emails are flooded with tons of information, notices, changes of terms, and so on.
At least I have more than 2,000 unread messages from the services. Some are about providing more details (the one I recently got from Revolut), the need to take action with my account, and so on.
That was the hole used for fraud. When you got an email from, let’s imagine, your bank, you were likely to take action without paying time to verify whether this email was legit.
Now, blue checkmarks are here to protect you; when you see them, that’s the sign that the domain used to create an email address and the logo is verified.
How do Gmail checkmarks work?
Blue checkmarks in Gmail require three layers of protection to verify an email address.
Google uses Brand Indicators for Message Identification (BIMI) feature, which requires senders to use strong authentication and verify their brand logo in order to display it as an avatar in emails. But before identify under BIMI, the sender should implement DMARC (Domain-based Message Authentication, Reporting & Conformance) policy, which includes:
- Setting up SPF (Sender Policy Framework).
Sender Policy Framework (SPF) is an email authentication method designed to prevent spammers from sending emails on behalf of other domains.
In simple terms, it works by allowing a domain to specify which mail servers are authorized to send email on its behalf. When receiving servers get an email, they check the SPF record of the sending domain to determine whether the email is from an authorized server; if it isn’t, the email can be marked as spam or rejected outright.
- DomainKeys Identified Mail (DKIM) authentication from senders to show the checkmark.
DomainKeys Identified Mail (DKIM) allows one to check if the domain indeed sent the email it claims to come from and verifies that the content has not been changed or tampered with during transit.
It does this by attaching a digital signature to the headers of an email message, which is generated using a private key only known to the sender’s domain.
The receiver then retrieves the corresponding public key from the sender’s DNS records and uses it to verify the signature, ensuring the email’s authenticity and integrity.
In other words, SPF and DKIM are designed to prevent fake emails that claim to be sent from a reputable domain or domain that looks almost the same but has slightly different spelling (tab-tw.com instead of tab-tv.com, and so on).
That was a hole usually used for fraud: you received an email that was created on the reputable domain (but that could be its subdomain) or the domain that looks almost the same.
- Also, the brand logo that’s displayed in an email should be verified under VMC (Verified Mark Certificate) authority.
Verified Mark Certificate (VMC) is a digital certificate that validates the ownership and authenticity of a logo or visual mark associated with an organization’s domain in an email message.
This certificate, issued by a trusted certificate authority, helps authenticate that the logo in an email is indeed from the claimed sender, not some sender that wants to mock it.
Can we trust them?
Both yes and no. Here’s my reasoning:
- Verification looks great when all trusted senders are verified. Blue checkmarks were added in May 2023, so that’s okay that not all senders have verified their emails yet.
But things should change in the near future to make this system work as it should be. When I’m writing the article, even emails sent by Google aren’t verified.
That puts the whole system on the edge. Yes, verified emails are still better than unverified, but the state of things, when a lot of official emails come from unverified addresses, reduces the total impact of such a system.
When I receive an unverified email now, that doesn’t mean it can’t be trusted, as it can be sent by Google or any other sender that’s 100% percent legit. And therefore, users would pay less attention to the verification marks.
- Issues with verification trustworthiness. I’ve heard about 2 cases when the system was hacked. One of them is well described on 9to5Google (here). And after this, Google launched additional DKIM authentication to better secure emails sent with a blue checkmark.
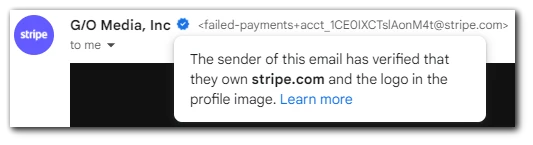
- Another issue is on the side of the senders, especially those that provide a lot of emails issued on their behalf, like Stripe (it’s used by many services to collect subscription payments). One such case is described on How-to-Geek (here); according to Google, the fake email verified by Stripe’s blue checkmark was authentic, so there was a bad actor on Stripe’s side.
That indicates another safety problem with the blue checkmarks system, as even if the email is verified, you’re not protected and can’t be aware of hacks and breaches on the verified sender’s side when the fraudsters act as bad actors on behalf of the verified sender.
Anyway, blue checkmarks can be trusted, but till now, you need to pay attention even to verified emails and double-check them, as there are still ways to fraud.
In the future, when more senders will get verification, the overall trustworthiness of a system will increase, as most of the senders will be verified. But now, even such reputable senders as Google hasn’t verified all emails they use to send notifications, alerts, and other emails.
Another problem is the overall complexity of the verification process, and there’s nothing Google can do about this. But this may lead to a situation when many senders won’t verify their emails, which takes a lot of time and back-end work.
I think Google should take the lead on this process, pushing companies to obtain checkmarks so that they would become an industry standard.